Table of Contents
Windows - CLI
Open CMD as System Account
PsExec is required.
PsExec -s cmd
Check Remote NTP Server
The following command will contact the NTP server 192.0.2.1 and show you 5 samples by printing time and offset.
w32tm /stripchart /computer:192.0.2.1 /dataonly /samples:5
Example with output.
PS C:\> w32tm /stripchart /computer:192.0.2.1 /dataonly /samples:5 Tracking 192.0.2.1 [192.0.2.1:123]. Collecting 5 samples. The current time is 18.04.2024 10:04:19. 10:04:19, -191.1682338s 10:04:21, -191.1659023s 10:04:23, -191.1665833s 10:04:25, -191.1664487s 10:04:27, -191.1664522s
Show Time Source
Show the current time source.
w32tm /query /status
Example: NTP time source with server 192.0.2.1.
PS C:\> w32tm /query /status Leap Indicator: 0(no warning) Stratum: 3 (secondary reference - syncd by (S)NTP) Precision: -23 (119.209ns per tick) Root Delay: 0.0133334s Root Dispersion: 0.0289849s ReferenceId: 0xC0A80101 (source IP: 192.0.2.1) Last Successful Sync Time: 25.04.2024 19:12:36 Source: 192.0.2.1 Poll Interval: 10 (1024s)
Set NTP Servers
Set your NTP servers manually, separated by space if more than one.
w32tm /config /manualpeerlist:"192.0.2.1 192.0.2.2" /syncfromflags:manual /update
More information: learn.microsoft.com: Windows Time service tools and settings
Disable Recall
Dism /Online /Disable-Feature /Featurename:Recall
Show Error Messages
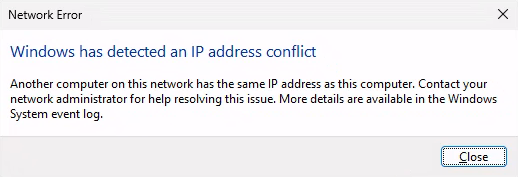
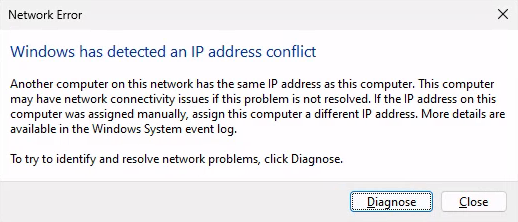
Interesting but useless, except you want to put it in AutoRun to troll people.
rundll32.exe ndfapi.dll, NdfRunDllDuplicateIPDefendingSystem
rundll32.exe ndfapi.dll, NdfRunDllDuplicateIPOffendingSystem
Source: Twitter